11.3. The Promise of Open Source
Telephony
Every good work of software starts by scratching
a developer's personal itch.
Eric S. Raymond, The
Cathedral and the Bazaar
In his book The
Cathedral and the Bazaar (O'Reilly), Eric S. Raymond
explains that "Given enough eyeballs, all bugs are shallow." The
reason open source software development produces such consistent
quality is simple: crap can't hide.
11.3.1. The Itch That Asterisk
Scratches
In this era of custom database and web site
development, people are not only tired of hearing that their
telephone system "can't do that," they quite frankly just don't
believe it. The creative needs of the customers, coupled with the
limitations of the technology, have spawned a type of creativity
born of necessity: telecom engineers are like contestants in an
episode of "Junkyard Wars," trying to create functional devices out
of a pile of mismatched components.
The development methodology of a proprietary
telephone system dictates that it will have a huge number of
features, and that the number of features will in large part
determine the price. Manufacturers will tell you that their
products give you hundreds of features, but if you only need five
of them, who cares? Worse, if there's one missing feature you
really can't do without, the value of that system will be diluted
by the fact that it can't completely address your needs.
The fact that a customer might only need five
out of five hundred features is ignored, and that customer's desire
to have five unavailable features that address the needs of his
business is dismissed as unreasonable. Until flexibility becomes
standard, telecom will remain stuck in the last centuryall the VoIP
in the world notwithstanding.
Asterisk addresses that problem directly, and
solves it in a way that few other telecom systems can. This is
extremely disruptive technology, in large part because it is based
on concepts that have been proven time and time again: "the
closed-source world cannot win an evolutionary arms race with
open-source communities that can put orders of magnitude more
skilled time into a problem."
11.3.2. Open Architecture
One of the stumbling blocks of the traditional
telecommunications industry has been its apparent refusal to
cooperate with itself. The big telecommunications giants have all
been around for over a hundred years. The concept of closed,
proprietary systems is so ingrained in their culture that even
their attempts at standards compliancy are tainted by their desire
to get the jump on the competition, by adding that one feature that
no one else supports. For an example of this thinking, one simply
has to look at the VoIP products being offered by the telecom
industry today. While they claim standards compliance, the thought
that you would actually expect to be able to connect a Cisco phone
to a Nortel switch, or that an Avaya voicemail system could be
integrated via IP to a Siemens PBX, is not one that bears
discussing.
In the computer industry, things are different.
Twenty years ago, if you bought an IBM server, you needed an IBM
network and IBM terminals to talk to it. Now, that IBM server is
likely to interconnect to Dell terminals though a Cisco network
(and run Linux, of all things). Anyone can easily think of
thousands of variations on this theme. If any one of these
companies were to suggest that we could only use their products
with whatever they told us, they would be laughed out of
business.
The telecommunications industry is facing the
same changes, but it's in no hurry to accept them. Asterisk, on the
other hand, is in a big hurry to not only accept change, but
embrace it.
Cisco, Nortel, Avaya, and Polycom IP phones (to
name just a few) have all been successfully connected to Asterisk
systems. There is no other PBX in the world today that can make
this claim. None.
Openness is the power
of Asterisk.
11.3.3. Standards Compliance
In the past few years, it has become clear that
standards evolve at such a rapid pace that to keep up with them
requires an ability to quickly respond to emerging technology
trends. Asterisk, by virtue of being an open source,
community-driven development effort, is uniquely suited to the kind
of rapid development that standards compliance demands.
Asterisk does not focus on cost-benefit analysis
or market research. It evolves in response to whatever the
community finds excitingor necessary.
11.3.4. Lightning-Fast Response to New
Technologies
After Mark Spencer attended his first SIP
Interoperability Test (SIPIT) event,
he had a rudimentary but working SIP stack for Asterisk coded
within a few days. This was before SIP had emerged as the protocol
of choice in the VoIP world, but he saw its value and momentum and
ensured that Asterisk would be ready.
This kind of foresight and flexibility is
typical in an open-source development community (and very unusual
in a large corporation).
11.3.5. Passionate Community
The Asterisk-users list receives over three
hundred email messages per day. Over ten thousand people are
subscribed to it. This kind of community support is unheard of in
the world of proprietary telecommunications, while in the open
source world it is commonplace.
The very first AstriCon event was expected to
attract one hundred participants. Nearly five hundred showed up
(far more wanted to but couldn't attend). This kind of community
support virtually guarantees the success of an open source
effort.
11.3.6. Some Things That Are Now
Possible
So what sorts of things can be built using
Asterisk? Let's look at some of the things we've come up with.
11.3.6.1. Legacy PBX migration
gateway
Asterisk can be used as a fantastic bridge
between an old PBX and the future. You can place it in front of the
PBX as a gateway (and migrate users off the PBX as needs dictate),
or you can put it behind the PBX as a peripheral application
server. You can even do both at the same time, as shown in
Figure
11-1.
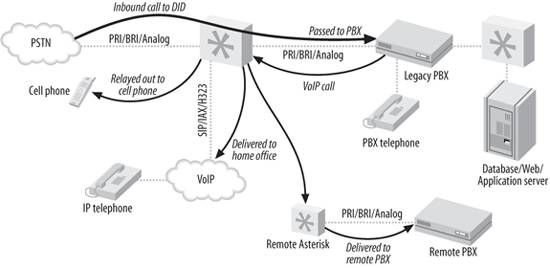
Here are some of the options you can
implement:
Keep your old
PBX, but evolve to IP
-
Companies that have spent vast sums of money in
the past few years buying proprietary PBX equipment want a way out
of proprietary jail, but they can't stomach the thought of throwing
away all of their otherwise functioning equipment. No
problemAsterisk can solve all kinds of problems, from replacing a
voicemail system to providing a way to add IP-based users beyond
the nominal capacity of the system.
Find-me-follow-me
-
Provide the PBX a list of numbers where you can
be reached, and it will ring them all whenever a call to your DID
(Direct Inward Dialing, a.k.a. phone number) arrives. Figure 11-2 illustrates
this technology.
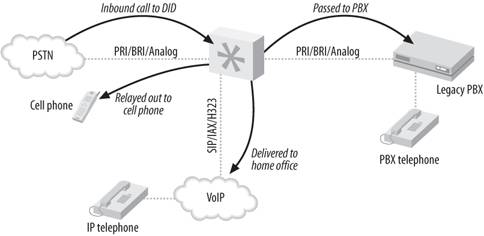
VoIP
calling
-
If a legacy telephony connection from an
Asterisk PBX to an old PBX can be established, Asterisk can provide
access to VoIP services, while the old PBX continues to connect to
the outside world as it always has. As a gateway, Asterisk simply
needs to emulate the functions of the PSTN, and the old PBX won't
know that anything has changed. Figure 11-3 shows how you can use
Asterisk to VoIP-enable a legacy PBX.
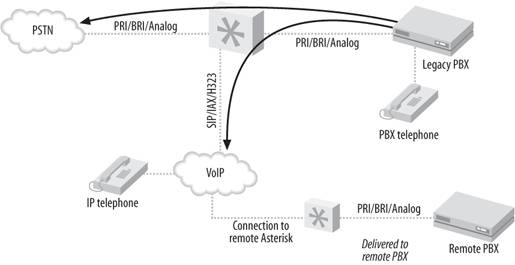
11.3.6.2. Low-barrier IVR
Many people confuse the term "Interactive Voice
Response," or IVR, with the Automated Attendant (AA). Since the
Automated Attendant was the very first thing IVR was used for, this
is understandable. Nevertheless, to the telecom industry, the term
IVR represents far more than an AA. An AA generally does little
more than present a way for callers to be transferred to
extensions, and it is built into most proprietary voicemail
systemsbut IVR can be so much more.
IVR systems are generally very expensive, not
only to purchase, but also to configure. A custom IVR system will
usually require connectivity to an external database or
application. Asterisk is arguably the perfect IVR, as it embraces
the concepts of connectivity to databases and applications at its
deepest level.
Here are a few examples of relatively simple
IVRs an Asterisk system could be used to create:
Weather
reporting
-
Using the Internet, you can obtain text-based
weather reports from around the world in a myriad of ways.
Capturing these reports and running them through a purpose-built
parser (Perl would probably eat this up) would allow the
information to be available to the dialplan. Asterisk's sound
library already contains all the required prompts, so it would not
be an onerous task to produce an interactive menu to play current
forecasts for anywhere in the world.
Math
programs
-
Ed Guy of Pulver.com did a presentation at
Astricon 2004 in which he talked about a little math program he'd
cooked up for his daughter to use. The program took him no more
than an hour to write. What it did was present her with a number of
math questions, the answers to which she keyed into the telephone.
When all the questions were tabulated, the system presented her
with her score. This extremely simple Asterisk application would
cost tens of thousands of dollars to implement on any closed PBX
platform, assuming it could be done at all. As is so often the case,
things that are simple for Asterisk would be either impossible or
massively expensive with any other IVR system.
Distributed
IVR
-
The cost of a proprietary IVR system is such
that when a company with many small retail locations wants to
provide IVR, it is forced to transfer callers to a central server
to process the transactions. With Asterisk, it becomes possible to
distribute the application to each node, and thus handle the
requests locally. Literally thousands of little Asterisk systems
deployed at retail locations across the world could serve up IVR
functionality in a way that would be impossible to achieve with any
other system. No more long-distance transfers to a central IVR
server, no more huge trunking facility dedicated to the taskmore
power with less expense.
These are three rather simple examples of the
potential of Asterisk.
11.3.6.3. Conference rooms
This little gem is going to end up being one of
the killer functions of Asterisk. In the Asterisk community,
everyone finds themselves using conference rooms more and
more, for purposes such as these:
-
Small companies need an easy way for business
partners to get together for a chat
-
Sales teams have a meeting once per week where
everyone can dial in from wherever they are
-
Development teams designate a common place and
time to update each other on progress
11.3.6.4. Home automation
Asterisk is still too much of an über-geek's
tool to be able to serve in the average home, but with no more than
average Linux and Asterisk skills, the following things become
plausible:
Monitoring the
kids
-
Parents who want to check up on the babysitter
(or the kids home alone) could dial an extension context protected
by a password. Once authenticated, a two-way audio connection would
be created to all the IP phones in the house, allowing mom and dad
to listen for trouble. Creepy? Yes. But an interesting concept
nonetheless.
Locking down
your phones
-
Going out for the night? Don't want the
babysitter tying up the phone? No problem! A simple tweak to the
dialplan, and the only calls that can be made are to 911, your cell
phone, and the pizza parlor. Any other call attempt will get the
recording "We are paying you to babysit our kids, not make personal
calls."
Pretty evil, huh?
Controlling the
alarm system
-
You get a call while on vacation that your mom
wants to borrow some cooking utensils. She forgot her key, and is
standing in front of the house shivering. Piece of cake; a call to
your Asterisk system, a quick digit string into the context you
created for the purpose, and your alarm system is instructed to
disable the alarm for 15 minutes. Mom better get her stuff and get
out quick, though, or the cops'll be showing up!
Managing
teenagers' calls
-
How about allocating a specific phone-time limit
to your teenagers? To use the phone, they have to enter their
access codes. They can earn extra minutes by doing chores, scoring
all As, dumping that annoying bum with the bad haircutyou get the
idea. Once they've used up their minutes... click... you get your
phone back.
Incoming calls can be managed as well, via
Caller ID. "Donny, this is Suzy's father. She is no longer
interested in seeing you, as she has decided to raise her standards
a bit. Also, you should consider getting a haircut."
 |

